Filter by Set
Conditional Access
Share
Share this Set
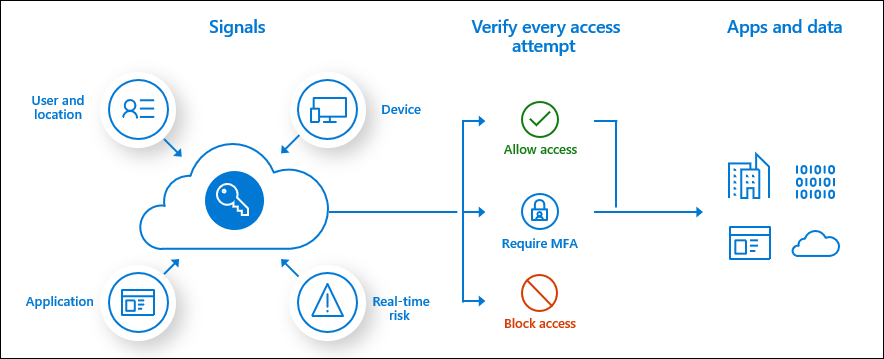
The modern security perimeter now extends beyond an organization's network to include user and device identity. Organizations can use identity-driven signals as part of their access control decisions.
...see more
Azure AD Conditional Access is at the heart of the new identity-driven control plane.
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action. Example: A payroll manager wants to access the payroll application and is required to do multi-factor authentication to access it.
Conditional Access policies are enforced after first-factor authentication is completed. Conditional Access isn't intended to be an organization's first line of defense for scenarios like denial-of-service (DoS) attacks, but it can use signals from these events to determine access.
...see more
Many organizations have common access concerns that Conditional Access policies can help with such as:
- Requiring multi-factor authentication for users with administrative roles
- Requiring multi-factor authentication for Azure management tasks
- Blocking sign-ins for users attempting to use legacy authentication protocols
- Requiring trusted locations for Azure AD Multi-Factor Authentication registration
- Blocking or granting access from specific locations
- Blocking risky sign-in behaviors
- Requiring organization-managed devices for specific applications
- .NET
- .NET
- .NET 6.0 Migration
- .NET Argument Exceptions
- .NET Class Library
- .NET Reflection
- 5 Best websites to read books online free with no downloads
- 5 surprising things that men find unattractive
- 5 Ways To Take Control of Overthinking
- 6 simple methods for a more productive workday
- 6 Ways To Stop Stressing About Things You Can't Control
- Add React to ASP.NET Core
- Adding reCAPTCHA to a .NET Core Web Site
- Admin Accounts
- Adobe Acrobat
- Afraid of the new job? 7 positive tips against negative feelings
- Agile
- AI
- AKS and Kubernetes Commands (kubectl)
- API Lifecycle Management
- Application Insights
- arc42
- Article Writing Tools
- ASP.NET Core Code Snippets
- ASP.NET Core Performance Best Practices
- ASP.NET Core Razor Pages and Markup
- ASP.NET Razor Syntax Cheat Sheet
- Asynchronous programming
- Atlassian
- Authorization Code Grant
- Avoiding List Reference Issues in .NET: Making Independent Copies
- AWS vs Azure vs GCP: Which Is Better?
- Axios Library
- Azure
- Azure API Management
- Azure App Registration
- Azure Application Gateway
- Azure Application Insights
- Azure Arc
- Azure Arc Commands
- Azure Architectures
- Azure Bastion
- Azure Bicep
- Azure CLI Commands
- Azure Cloud Products
- Azure Cognitive Services
- Azure Container Apps
- Azure Cosmos DB
- Azure Cosmos DB Commands
- Azure Costs
- Azure Daily
- Azure Daily 2022
- Azure Daily 2023
- Azure Data Factory
- Azure Database for MySQL
- Azure Databricks
- Azure Diagram Samples
- Azure Durable Functions
- Azure Firewall
- Azure Functions
- Azure Kubernetes Service (AKS)
- Azure Landing Zone
- Azure Log Analytics
- Azure Logic Apps
- Azure Maps
- Azure Monitor
- Azure News
- Azure PowerShell Cmdlets
- Azure PowerShell Login
- Azure Private Link
- Azure Purview
- Azure Redis Cache
- Azure Security Groups
- Azure Sentinel
- Azure Service Bus
- Azure Service Bus Questions (FAQ)
- Azure Services Abstract
- Azure SQL
- Azure Storage Account
- Azure Tips and Tricks
- Backlog Items
- BASH Programming
- Best LinkedIn Tips (Demo Test)
- Best Practices for RESTful API
- Bing Maps
- Birthday Gift Ideas for Wife
- Birthday Poems
- Black Backgrounds and Wallpapers
- Bootstrap Templates
- Brave New World
- Break Out of a JavaScript Loop
- Brian Tracy Quotes
- Build Websites Resources
- C# - Data Types
- C# Code Samples
- C# Design Patterns
- C# Development Issues
- C# Programming Guide
- C# Retry Pattern
- C# Strings
- Caching
- Caching Patterns
- Camping Trip Checklist
- Canary Deployment
- Careers of the Future You Should Know About
- Cheap Vacation Ideas
- Cloud Computing
- Cloud Migration Methods
- Cloud Native Applications
- Cloud Service Models
- Cloudflare
- Code Snippets
- Compelling Reasons Why Money Can’t Buy Happiness
- Conditional Access
- Configurations for Application Insights
- Const in JavaScript
- Create a Routine
- Create sitemap.xml in ASP.NET Core
- Creative Writing: Exercises for creative texts
- CSS Selectors Cheat Sheet
- Cultivate a Growth Mindset
- Cultivate a Growth Mindset by Stealing From Silicon Valley
- Custom Script Extension for Windows
- Daily Scrum (Meeting)
- Dalai Lama Quotes
- Data Generators
- DataGridView
- Decision Trees
- Deployments in Azure
- Dev Box
- Develop ASP.NET Core with React
- Docker
- Don’t End a Meeting Without Doing These 3 Things
- Drink More Water: This is How it Works
- Dropdown Filter
- Earl Nightingale Quotes
- Easy Steps Towards Energy Efficiency
- EF Core
- EF Core Migrations
- EF Core Save Data
- Elon Musk
- Elon Musk Companies
- Employment
- English
- Escape Double Quotes in C#
- Escaping characters in C#
- Executing Raw SQL Queries using Entity Framework Core
- Factors to Consider While Selecting the Best Earthmoving System
- Feng Shui 101: How to Harmonize Your Home in the New Year
- Filtering and Organizing Data with JavaScript
- Flying Machines
- Foods against cravings
- Foods that cool you from the inside
- Four Misconceptions About Drinking
- Free APIs
- Funny Life Quotes
- Generate Faces
- Generate Random Numbers in C#
- Genius Money Hacks for Massive Savings
- Git Cheat Sheet
- git config
- Git for Beginners
- Git Fork
- GitHub
- GitHub Concepts
- Green Careers Set to Grow in the Next Decade
- Grouping in EF Core
- Habits Of Highly Stressed People and how to avoid them
- Happy Birthday Wishes & Quotes
- Helm Overview
- How to Clean Floors – Tips & Tricks
- How to invest during the 2021 pandemic
- How To Make Money From Real Estate
- How To Stop Drinking Coffee
- HTML 'video' Tag
- HTTP
- HTTP PUT
- HTTP Status Code
- Image for Websites
- Implementing Efficient Search Functionality in React
- Inspirational Quotes
- Install PowerShell
- Iqra Technology, IT Services provider Company
- JavaScript
- JavaScript Array Object
- JavaScript Collection
- JavaScript Functions
- JavaScript Scope
- JavaScript Snippets
- JavaScript Tutorial
- JavaScript Variables
- Jobs Of 2050
- jQuery
- jQuery plugins
- JS Async
- JSON (JavaScript Object Notation)
- JSON Deserialization in C#
- JSON for Linking Data (JSON-LD)
- Json to C# Converters
- JSON Tree Viewer JavaScript Plugin
- JSON Web Tokens, (JWT)
- Karen Lamb Quotes
- Kubernetes Objects
- Kubernetes Tools
- Kusto Query Language
- Lack of time at work? 5 simple tricks to help you avoid stress
- Lambda (C#)
- Last Minute Travel Tips
- Last-Minute-Reisetipps
- Latest Robotics
- LDAP
- LDAP search filters
- Leadership
- Let in JavaScript
- List Of Hobbies And Interests
- Logitech BRIO Webcam
- Magento vs Shopify - Which eCommerce Platform is Best?
- Management
- Managing Services with PowerShell: A Quick Guide
- Mark Twain Quotes
- Markdown
- Meet Sophia
- Message-Oriented Architecture
- Microservices
- Microsoft Power Automate
- Microsoft SQL Server
- Microsoft Teams
- Migrations VS Commands
- Mobile UI Frameworks
- Motivation
- Multilingual Applications
- NuGet
- Objectives and Key Results (OKR)
- Objectives and Key Results (OKR) Samples
- OKR Software
- Online JSON Viewer and Parser
- Operators
- Outlook Automation
- PCMag
- Phases of any relationship
- Playwright
- Popular cars per decade
- Popular Quotes
- PowerShell
- PowerShell Array Guide
- PowerShell Cmdlets
- PowerShell Coding Samples
- PowerToys
- Prism
- Pros & Cons Of Alternative Energy
- Quill Rich Text Editor
- Quotes
- RACI Matrix
- Razor Syntax
- React Click Event Handlers
- React Conditional Rendering
- React Context
- React Hooks
- React Router
- Reasons why singletasking is better than multitasking
- Regular Expression (RegEx)
- Reorder List in JavaScript
- Resize Images in C#
- Response Caching in ASP.NET Core
- RESTful APIs
- Rich Text Editors
- Rob Siltanen Quotes
- Robots
- Run sudo commands
- Salesforce Offshore Support Services Provider
- Salesforce Offshore Support Services Providers
- Sample Data
- Save Money On Food
- Score with authenticity in the job interview
- Scrum
- Scrum Meetings
- Security
- Semantic Versioning
- Serialization using Thread Synchronization
- Service Worker
- Snipps
- Speak and Presentation
- Sprint Backlog
- SQL Functions
- SQL References
- SQL Server Full-Text Search
- SQL UPDATE
- Stress
- Successful
- Surface Lineup 2021
- Surface Lineup 2021 Videos
- SVG Online Editors
- TanStack Query (FKA React Query)
- Team Manifesto
- Technologies
- Technologies
- Technology Abbreviations
- Technology Glossary
- TechSpot
- That is why you should drink cucumber water every day
- The Cache Tag Helper in ASP.NET Core
- The Verge
- Theodore Roosevelt Quotes
- These 7 things make you unattractive
- Things Successful People Do That Others Don’t
- Things to Consider for a Great Birthday Party
- Things to Consider When Designing A Website
- Thoughts
- TinyMCE Image Options
- TinyMCE Toolbar Options
- Tips for a Joyful Life
- Tips for fewer emails at work
- Tips for Making Better Decisions
- Tips for Managing the Stress of Working at Home
- Tips for Writing that Great Blog Post
- Tips On Giving Flowers As Gifts
- Tips you will listen better
- Top Fitness Tips
- Top Healthy Tips
- Top Money Tips
- Top Ten Jobs
- Track Authenticated Users in Application Insights
- Transactions in EF Core
- Unicode Characters
- Uri Class
- useContext Hook in React
- Var in JavaScript
- Visual Studio 2022
- Vital everyday work: tips for healthy work
- Walking barefoot strengthens your immune system
- Walt Disney Quotes
- Ways for Kids to Make Money
- Web Design Trends & Ideas
- Web Icons
- Web Scraping
- Webhooks
- Website Feature Development
- What are my options for investing money?
- What happens when you drink water in the morning
- What is a Sprint in Scrum?
- What Is Stressful About Working at Home
- What To Eat For Lunch
- When to use Task.Delay, when to use Thread.Sleep?
- Why Vue JS Is the Perfect Choice for Frontend Development
- Windows
- Windows 11 Top Features You Should Know
- Winston Churchill Quotes
- XPath
- You'll burn out your team with these 5 leadership mistakes
- ZDNet