Successfully added
Azure
by Doug
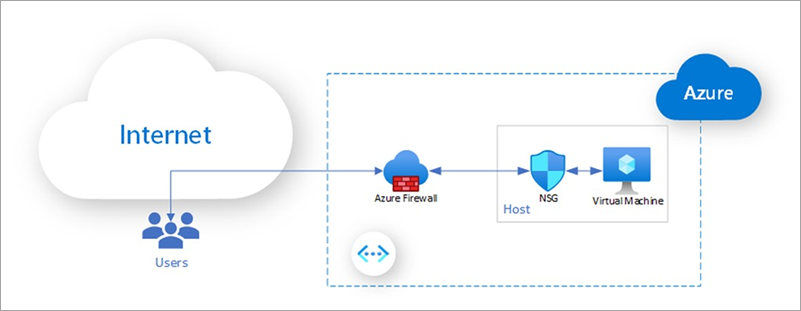
Enabling Zero Trust with Azure network security services
Microsoft’s Zero Trust Framework protects assets anywhere by adhering to three principles:
- Verify explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least privileged access: Limit user access with just-in-time and just-enough-access (JIT and JEA), risk-based adaptive policies, and data protection to help secure both data and productivity.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Enabling Zero Trust with Azure network security services | Azure Blog and Updates | Microsoft Azure
Referenced in:
Comments