Successfully added
Security
by Jorge
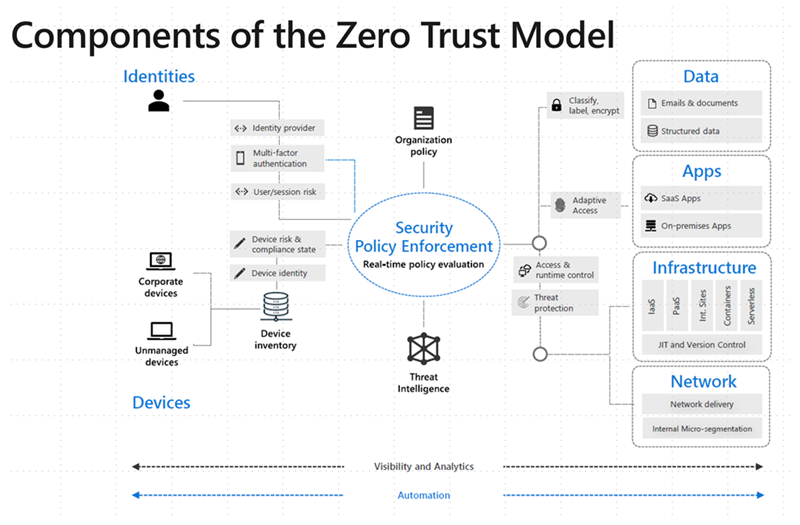
Components of the Zero Trust Model
Zero Trust defined
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real-time.
Microsoft
Microsoftsecurity
Zerotrustsecurity
Referenced in:
Comments